
Hashcat is an industry standard when it comes to password cracking and recovery. Hashcat is touted as being the worlds fastest and most advanced password recovery utility, and it certinly lives up to its reputation. Although it started out as a proprietary software, it was later released as an open source tool and remains so to this day. It continues to be updated and supported by Team Hashcat.
In the guide we will go over the basics of using hashcat. Make no mistake, hashcat isn't a program that you learn in one day. There's simply to many options, modes, and techniques to learn at once. But this guide will give you enough information to get started with cracking and introduce you to some of the most common techniiques.
I'm going to make the foolish assumption that you have hashcat installed and working on your machine of choice. Depending on your setup, hashcat can sometimes be tricky to get working properly, usually due to a driver issue. Some distros such as Kali usually come with hashcat pre-installed. If you do not have hashcat installed, start by taking a look at their installation instructions on their webpage.
Assuming you now have hashcat running on your machine, lets get started. Open a terminal and type in the following:
(user@linux)-$ hashcat --help
This will display the hashcat help menu. Note that there is a ton of information in here! A better command to use would be the less command:
(user@linux)-$ hashcat --help | less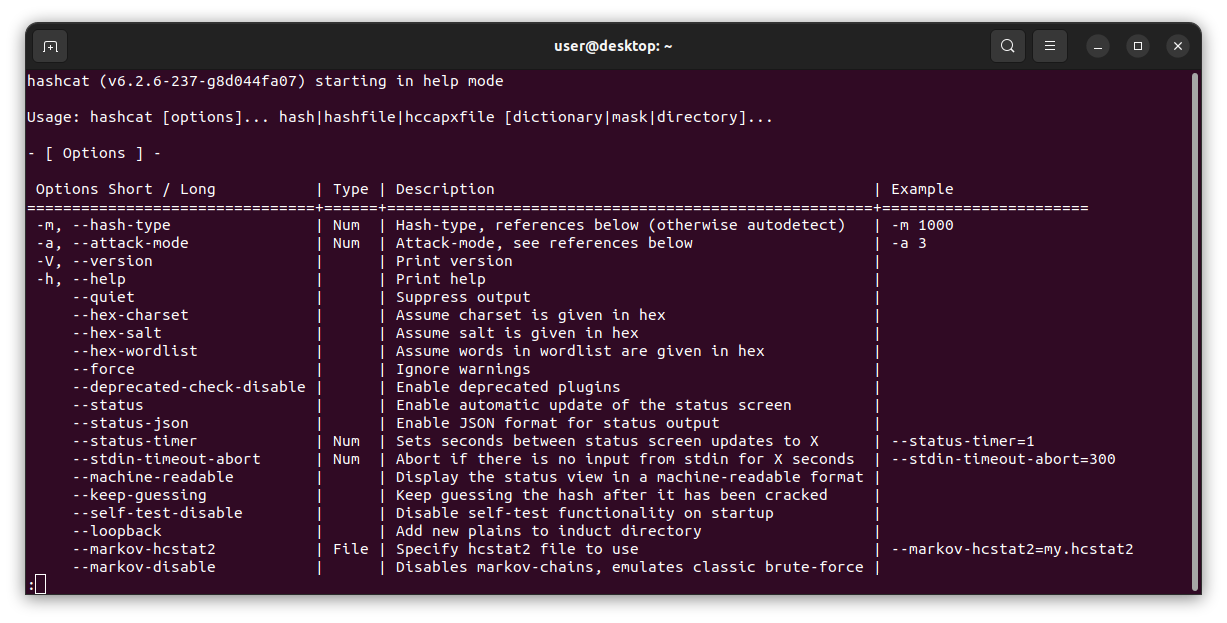
Using the less command will only display what will fit in your terminal. To see more or scroll down, press the space bar. At first glance, all this information will seem overwhelming. As mentioned earlier, hashcat is not something you learn in a day. But don't worry, after a few examples you will understand the basics well enough to make use of it. The first thing displayed in the hashcat help menu is the basic syntax, and available flags. The most important flags you should know for now are -m, which is hash-type, and -a which is attack-mode. There are other important flags that we will explore later.
If you scroll down a bit, you will see "Hash modes". This is a list of all the supported hash types and their reference number. In simple terms, when you are trying to crack a password you need to know what type of hash is it. For example, if you are trying to crack a a wifi password that uses the common wpa2 security, you would need to use the hash type 22000.
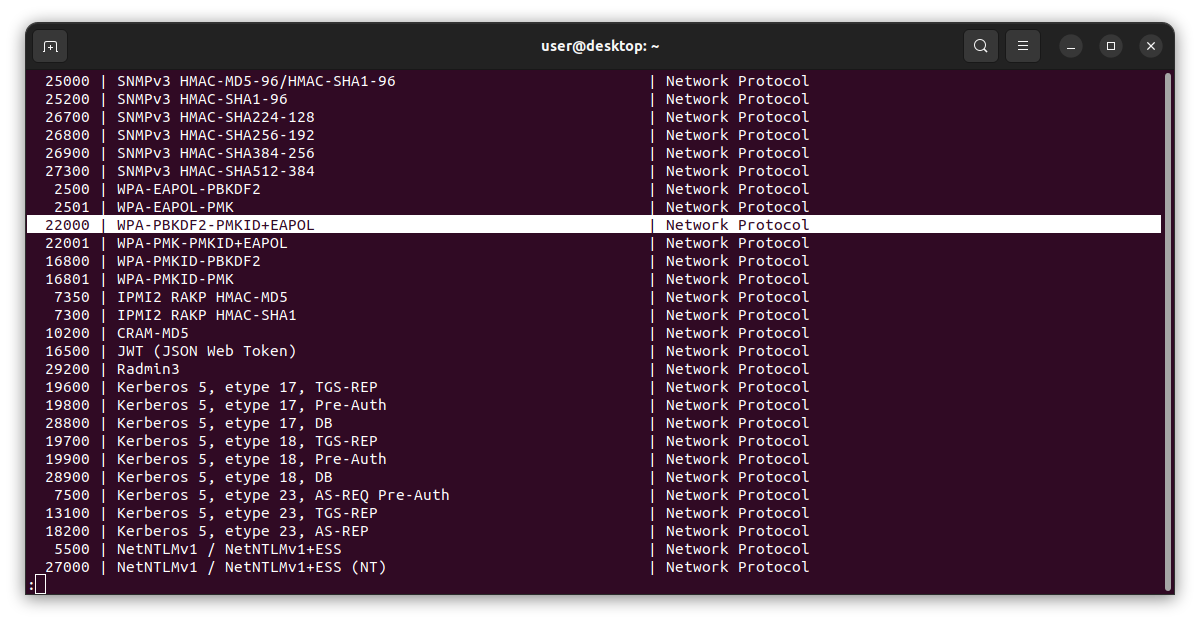
Hint: you can easily grep for certin types of hashes. For example: hashcat -hh | grep -i wpa
Moving down, we see the different types of attack-modes.
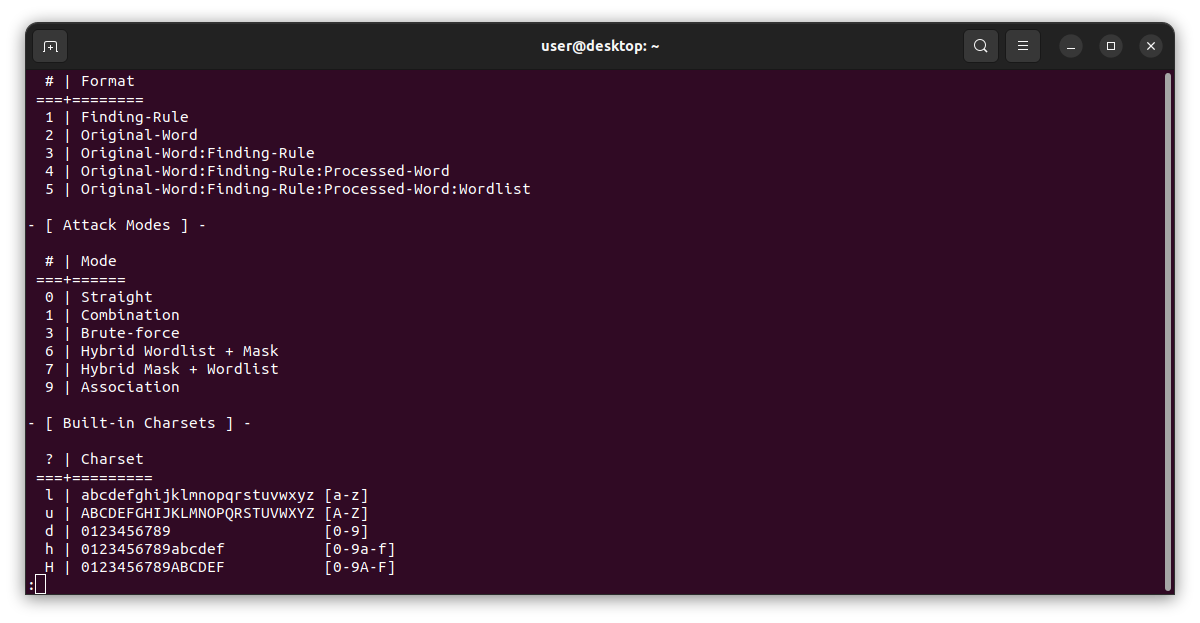
There are different methods used in password cracking, and the attack mode specifies which method you want to use. Typically, most beginners will start with what's known as a dictionary attack. This is attack mode 0 in hashcat, called straight. This type of attack is the least sophisticated but is usually the easiest and can work quite well in some situations. The basic primise of this technique is simple, you have a text file that contains a list of potential passwords, hashcat iterates through the entire list and checks for a match against the password hash. If it finds a match, it stops running and informs you of the password. You can easily obtain a list of common passwords(usually refered to as a wordlist or dictionary) from the web. One of the most famous wordlists is called the Rockyou wordlist. This is a list of about 14 million passwords that was leaked from a company called RockYou. The RockYou company did not protect their users data, and were subsiquintly hacked multiple times. Hackers than released all the users password. The RockYou company is long gone(go figure), but the password list lives on. Kali actually comes with this wordlist(along with others), you can find it in the /usr/share/wordlists/rockyou.txt.gz directory(just make sure you unzip it!). Under attack modes in the help menu, you will notice a Charset section. We will cover this later for attack mode 3, brute force.
Lets start with a basic dictionary attack. Make sure you have a wordlist downloaded for this. Check out weakpass.com if you don't have one already. For this guide I'll be using the Top 6 Million wordlist from weakpass. You will also need a password hash to crack. Lets start with a simple md5 hash, and then we'll move onto PBKDF2(used in wifi). We can easily make a MD5 password ourselves in linux. Open a terminal and type in the following:
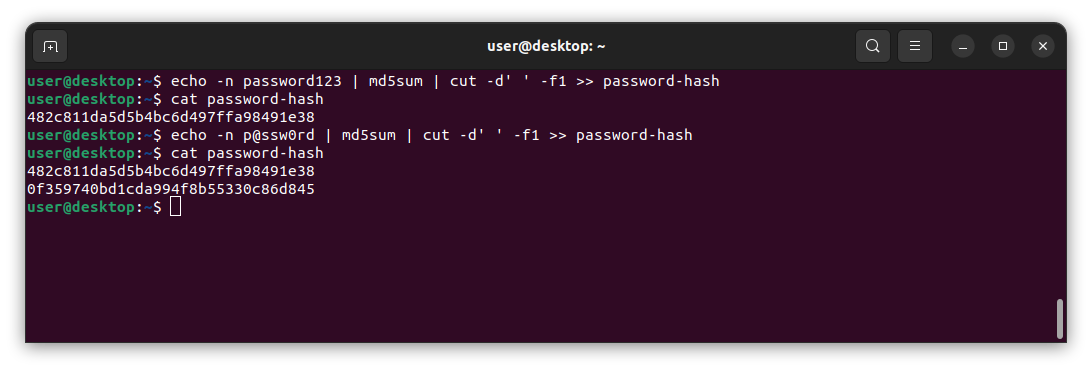
(user@linux)-$ echo -n password123 | md5sum | cut -d' ' -f1 >> password-hash
Here we are simplely using the echo command to echo a made up password(password123) to stdout, then we are pipping that into the md5sum command to convert it to a md5 hash. Next we are using the cut command to trim off the extra space at the end of the hash, and than we are redirecting that into a file, in this case called password-hash. If we cat this file we will see that it indeed contains a md5 hash of the password.
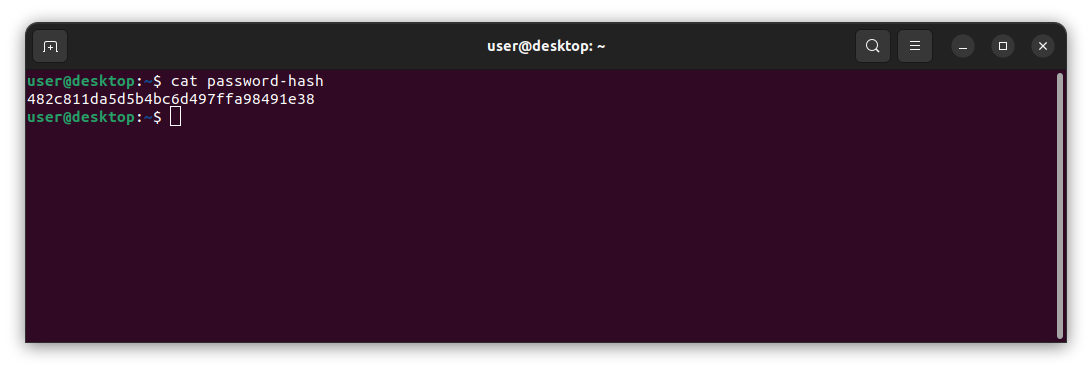
NOTE: a password hash is simply a way of changing a plain text password, such as "password123" into a seemingly random groupe of characters. Different types of hashes use different algorithms and offer various levels of security. Hashes are important because even if someone can gain access to a data-base that stores user passwords, such as banking website, the passwords are not stored in plain text, but rather in a secure hash.
If we wanted to add more passwords to this list we could run the previous command again and simplely change "password123" to another password, such as "p@ssw0rd". Just make sure you keep the double >> to append to the password-hash file and not overwrite it.
Now that we have a file containing some hashed passwords, we can run it through hashcat to crack it. In a terminal type the following:
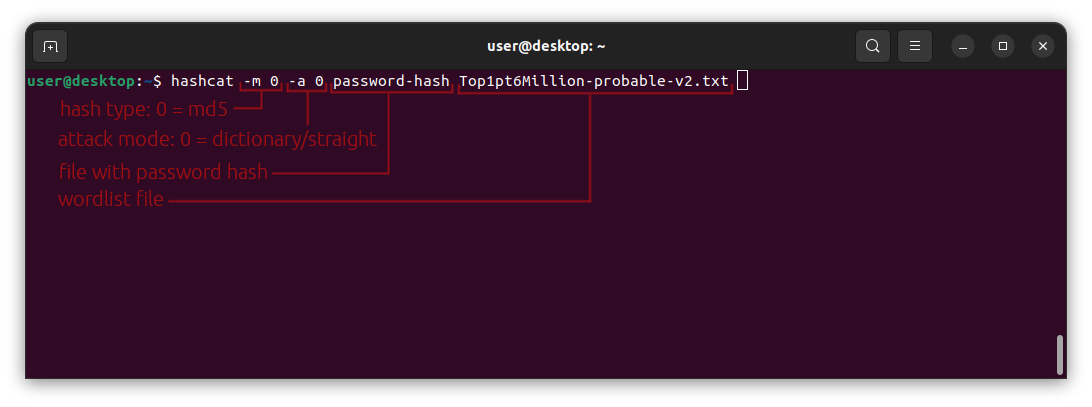
(user@linux)-$ hashcat -m 0 -a 0 password-hash Top1pt6Million-probable-v2.txt
We start by calling hashcat, then we specify the hash type with -m. The hash type for md5 is 0. Next we specify the attack mode with -a. The attack mode for a dictionary attack is 0. Next we specify our file that contains password(s), and than we specify what worldlist to use.
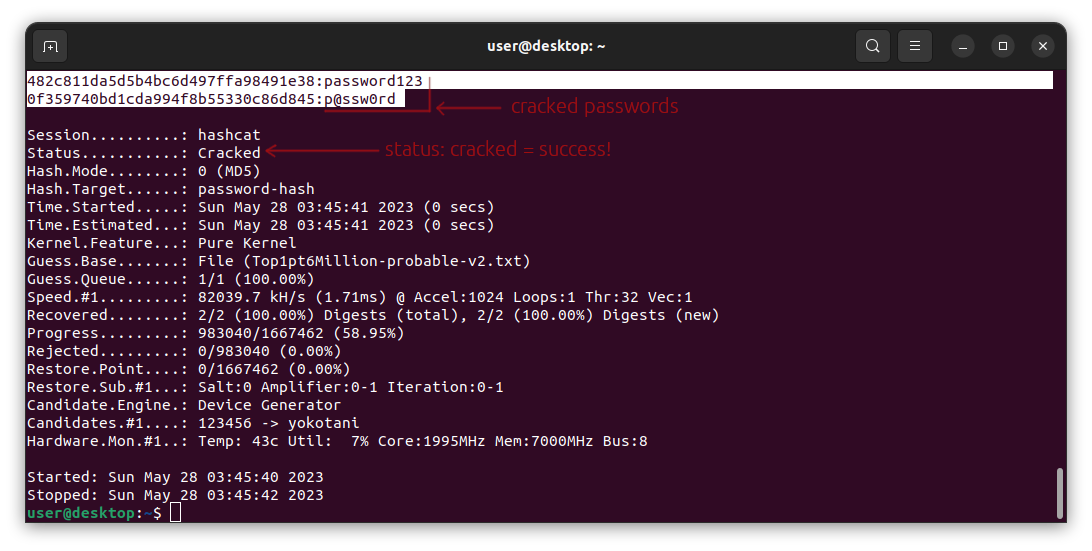
If things go right, hashcat will run sucsessfully. Hashcat displays a status while it is running. You can see an updated status anytime while it is running by pressing the s key on your keyboard. In this case, hashcat probably ran so fast that you didn't need to update the status. However, in more complex examples you will see how handy this feature is. As you can see in the above screenshot, the final status is Cracked. At the very top of the screen we can see that hashcat was indeed able to crack the hashes, as it prints out the actual passwords that we previously hashed with md5sum(password123 and p@ssw0rd). In Ubuntu, hashcat usually saves this potfile at ~/.local/share/hashcat/hashcat.potfile.
(user@linux)-$ cat ~/.local/share/hashcat/hashcat.potfile.
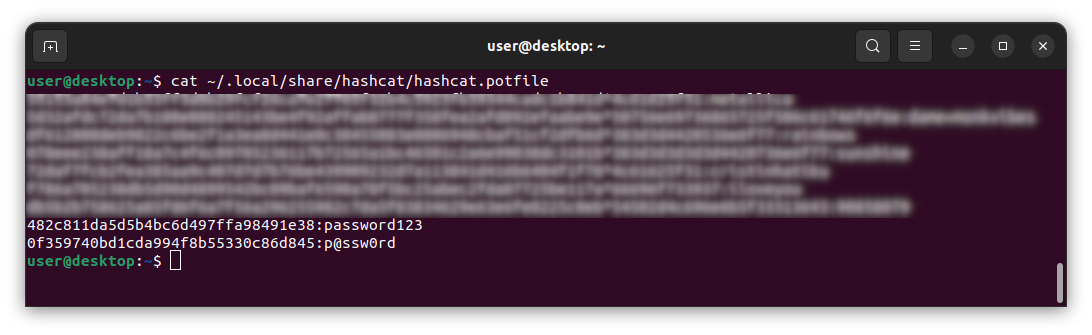
If you have been following along, congratulations! You just cracked a password with hashcat. Although this was a very simple one, it serves as a good starting point. You should now have a better understanding of using hashcat and it's syntax. In the next section we will crack a more advanced type of hash typically used with WiFi, and we will explore some slightly more advanced techniques.